Over the past century, warfare has increasingly been taking place on the electromagnetic spectrum. A century ago, primitive radio first gave commanders the ability to control forces at sea across great distances. Attempts to thwart enemy communication, or to turn it to one's own ends, swiftly followed. During WWI, both sides tried to jam the other's communication, and set up direction-finding networks to locate the source of transmissions. These set the pattern that has been followed with increasing sophistication ever since.

An RC-135 Rivet Joint, the premier USAF electronic intelligence aircraft
Electronic warfare is usually divided into three parts: Electronic Countermeasures (ECM), Electronic Counter-countermeasures (ECCM) and Electronic Support Measures (ESM).1 ECM is concerned with denying the enemy the use of the electromagnetic spectrum. This is conventionally done by jamming, the electronic equivalent of playing loud noise to drown out sounds you don't want someone else to hear. ECCM is a wide variety of techniques intended to mitigate the effects of ECM. If someone is playing white noise to stop you from hearing a specific note, it might be the use of a signal processor to listen to only the specific frequency you care about. ESM is primarily concerned with locating and characterizing the emitters of the other side. In our acoustic analogy, it would be learning the sounds of someone else's car so you can recognize them if they come after you, or using multiple microphones to locate someone trying to sneak up on you in the dark.
We'll start with ESM, which is critical to the effectiveness of ECM and ECCM. ESM covers a wide variety of techniques and goals, all of which are unified by the fact that they are concerned with passively gathering information on enemy emissions. This can mean anything from flying an airplane loaded with sensitive electronic receivers near the border of a potential enemy to gain information on the characteristics of their radars, to triangulating the radio signals of a command post so you can dump artillery on it, to a fighter listening for the radar signals of a SAM2 trying to target it. In exceedingly rough terms, half of the work of ESM consists of listening to learn what the other guy is doing with the electromagnetic spectrum, and the other half is using that information to figure out what he's doing in real time. There's a lot of overlap, and the whole field is as deeply classified as anything outside of cryptography and nuclear weapons.
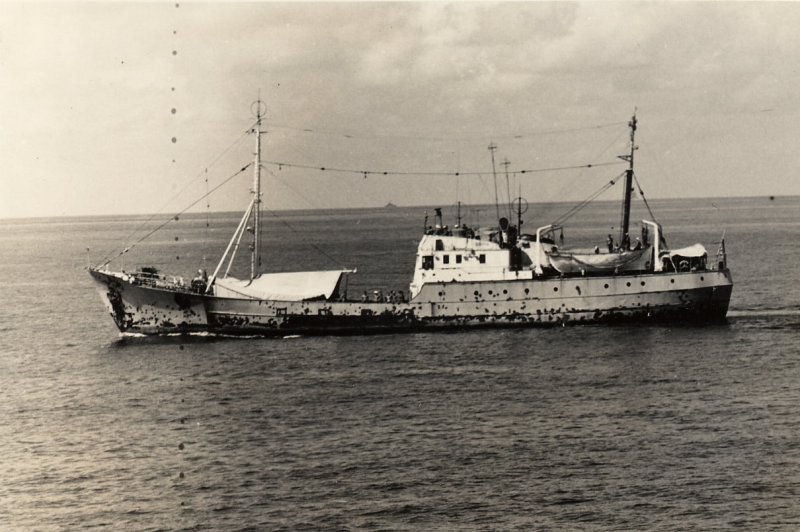
A Soviet "trawler" following a US carrier to gain electronic intelligence
The first stage of ESM is Electronic Intelligence or ELINT, part of Signals Intelligence.3 ELINT information comes from any number of platforms including satellites, aircraft, surface ships, ground-based listening posts and submarines. These pick up signals across the spectrum, providing information as mundane as the location of civilian navigation beacons and as vital as the basic signal characteristics of a new radar. Analysts can use that information to gain clues about its purpose. For instance, longer wavelengths are better for search, while shorter wavelengths give more precise positions for tracking. This information is combined with other facts, which might be from an agent or from a trade-show brochure, to give a decent picture of the radar's purpose. ELINT information is also used to build up an "Electronic Order of Battle", an outline of what systems a potential enemy has and how he expects to use them. This forms the basis of electronic warfare efforts on every level, from getting a picture of enemy plans and situations down to defeating missile attack. It also forms the basis of the ECM and ECCM plan, which we will discuss in later installments.4

USS Kincaid showing Outboard ESM system at the top of the foremast
Particularly at sea, ESM information is vital for gaining a picture of what the enemy is up to. During the Battle of the Atlantic, direction-finding of signals was vital to the Allied victory, and even today, interception of signals is still the most effective way to search the oceans. During the Cold War, the US put great emphasis on ESM systems for targeting Tomahawk Anti-Ship Missiles, and the missiles themselves were fitted with an ESM system so they could recognize major Soviet vessels after their half-hour flight to the target area. To thwart similar efforts on the part of the Soviets and make it harder to figure out who was who from ESM data in general, the USN fitted every major combatant with an AN/SPS-49 radar, allowing them to run a radar without giving away their identity. Even this might not be effective against the most modern ESM systems. Major military radars are essentially hand-built, and have subtle variations which can form a "fingerprint", allowing a specific platform to be recognized.
Lastly, there are the ESM systems which have direct tactical use, alerting the crew and combat systems of an aircraft or ship if there is a radar illuminating them. Usually, they have a threat library capable of basic target identification. At sea, these systems often automatically activate the jamming and decoy systems fitted to the vessel in question when they detect what they think is a missile homing head. Aircraft radar warning receivers alert the crew to the direction and type of threat, but usually leave the response up to them. The specifics of both responses, along with ECM in general, will be our subject next time.
1 For some reason, NATO has recently rechristened these Electronic Attack, Electronic Protection, and Electronic Warfare Support. Older sources and the vast majority of non-professional discussion will use the older terms, as will I. ⇑
2 Surface-to-air missile ⇑
3 Signals intelligence, or SIGINT, also covers communications interception, decryption, and the like. I'm going to ignore that aspect for now. ⇑
4 Because knowledge of a radar's characteristics is vital to countering it, many radars have what are known as War Emergency Modes, with slightly different characteristics. These are carefully concealed from satellites and other obvious snoopers, but they have to be tested at some point. Submarines are excellent platforms from which to observe these tests, and a significant fraction of the US attack submarine force is tasked with ELINT work. Today, it's fairly easy to update threat libraries and ECM gear because they're software-controlled, but until the 80s, most systems were hardwired. If a radar had a mode you didn't know about, then all the various EW gear would have to be returned to the factory to be updated to counter it, which could take months. ⇑
5 OK, these are fakes, installed after we got the ship. But I couldn't find a good photo of the real ones on any of the battleships. My photo. ⇑



Recent Comments